choose ESTA?
The simple nature of the software allows for easy integration into existing systems, as well as interoperability with other software solutions, whether they are legacy or bleeding edge products.
If your connection drops, ESTA will re-establish a connection when it can, and resume your transfer right where it left off, instead of restarting at the beginning, thus ensuring minimal bandwidth usage despite the stops and starts. ESTA does the heavy lifting for you, allowing you to focus on the data, instead of focusing on how to get it from place to place. No longer will you have to rely on stop-gap solutions and command line utilities. Set it up once, and itíll run forever.
ESTA owes its minimal bandwidth usage to data compression, a minimal binary transfer protocol, and its segmented transfer mechanism. These systems all act in concert to get your data there on time, intact, with minimal cost and maximum security. We do all of this while, at the same time, ensuring that the impact to your users is negligible. Performance is key in application scaling, and so the ESTA solution targets minimal memory usage, making sure that your users, applications, and servers are left to perform their primary functions, un-impacted by background file transfers.
ESTA has successfully transferred millions of files, a significant portion of which were delivered via satellite, all without a single loss of data.
Your data is secure against prying eyes, even over unreliable and untrusted network connections.
ESTA provides you with the most functionality, using minimal system resources, maximizing your investment.


Whether you are located out at sea, in the trenches, an industrial site, or simply the leisure of your own home, ESTA will ensure that all your file transfers are secure and reliable. Regardless of the scenario, ESTA is built to handle the most unreliable network conditions and operate with a low profile, providing results you can depend on without compromising your computer's performance.

ESTA transfers data in discreet chunks, using secure hash algorithms to validate data receipt, discover potential tampering, and minimize data retransmission in the event of corruption or disconnections. This allows us to resume a file transfer where it left off rather than start over from scratch, as is required by other older protocols.
This system also ensures maximum data integrity by validating data as it's received and written to the disk, and validating the whole file when the transfer completes, providing you with peace of mind, secure in the knowledge that your data is safe.
A secure TLS tunnel is used to protect all communications between peers. We implemented industry standard PKI infrastructure to provide reliable identification and secure communication, so you can rest comfortably knowing that your data goes where you want it to go, and nowhere else. High bit-depth asymmetric encryption algorithms provide a secure basis for peer identification and are used worldwide by critical security industries, including banking, health care, and even government security sectors.
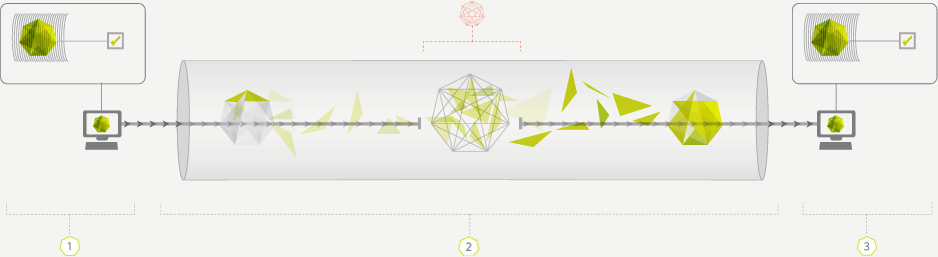
This shape represents a file that is transferred. It is made up of many pieces in a particular order.
ESTA maintains an image of what a file is supposed to look like when it's received. When your connection is dropped, data is never lost or corrupted.
These lines represent an internet connection as information is being transferred.
TLS tunnel is used to protect all communications between peers.


Logistical
Transfer your inventory data from warehouse to warehouse quickly and easily.
Military
Hostile work environment?
Get your data in, and out, safe
in the knowledge that no
one is listening.
Office
Securely transfer large files
to remote offices without
setting up complex
VPN tunnels.
Home
Too big for email? Too
urgent for snail mail?
We can help.


Simplicity Begets Productivity
And so Emprise Secure Transfer Agent doesn't require cumbersome client software for your users to move files around. Transferring files with ESTA can be accomplished by simply dragging and dropping files within the Microsoft Explorer file manager.
- Drag, drop, and done.
- File Explorer Interface.
Reliability Is
Absolutely Essential
Which is why Emprise Secure Transfer Agent ensures maximum data integrity by validating files before, during, and after transport. If you have an unreliable internet connection, ESTA will save you time and energy by resuming your file transfers exactly where they left off, instead of re-sending the entire file again.
- Automatic file resume.
- Periodic connection retries.
- Resumes exactly where it left off.
Security Is Imperative
Emprise Secure Transfer Agent uses the industry-standard TLS protocol to ensure that your files are safe from prying eyes, and a secure public/private-key based certificate system to ensure that your files aren't intercepted along the way. Detailed audit records are standard, logging every connection and more.
- 1024-bit or 2048-bit Public/Private key cryptography.
- Certificate based peer identification.
- TLS.
- FIPS Compliance Option.
- Detailed Audit Reports.
Flexibility Allows
For Future Expansion
Emprise Secure Transfer Agent's flexible routing system allows you to set up computers to be used as relay points, also known as hops or switching points. This allows you to manage the flow of files over network architectures which might not allow a direct connection between two computers.
- Dynamic message routing system.
- Multi-tiered options available